High-dimensional coherent one-way quantum key distribution

Introduction
Quantum key distribution (QKD) is an advanced technology that provides ultimate secure communication by exploiting quantum states of light as information carriers over communication channels1,2,3,4,5. In early QKD protocols, each bit of the key was encoded using a quantum state belonging to a two-dimensional Hilbert space6,7. High-dimensional QKD protocols were introduced and analyzed more recently, based on the preparation of a set of states belonging to a high-dimensional Hilbert space, called qudits8,9,10,11,12,13,14,15,16. The higher information capacity of qudits allows for a higher secure key rate and improves the robustness to noise, leading to higher threshold values of the quantum bit error rate (QBER)17,18.
Time-bin encoding of weak coherent laser pulses is the most popular technique for implementing QKD over single-mode fibers19,20,21,22. Recent proposals and demonstrations of high-dimensional temporal encoding showed a significant key rate improvement23,24,25,26,27,28,29,30,31. In particular, a record-breaking key rate of 26.2 Mbit/s was achieved with a four-dimensional time-bin protocol that is robust against the most general (coherent) attacks23. Furthermore, high-dimensional time-bin encoding was successfully demonstrated in entanglement-based QKD systems over free-space32 and fiber links33,34,35.
Implementation of high-dimensional QKD protocols in commercial systems is still held back since present high-dimensional schemes require significantly more complex experimental resources, relative to cost-effective two-dimensional systems36. The large experimental overhead results from the fact that high-dimensional encoding not only increases the channel capacity but also increases the amount of information that Eve can extract. Most QKD protocols limit the amount of information accessible to Eve by projecting the quantum states at the receiver’s end on unbiased bases. Although projection in two-dimensional schemes is usually implemented with a single interferometer followed by a single photon detector (SPD), to fully exploit the potential capacity of d-dimensional schemes, O(d) imbalanced interferometers and O(d) SPDs are required23,24,25. Thus, to date, all high-dimensional QKD systems implementations require complex and expensive systems that are impractical for commercial applications.
In this work, we present a different approach for high-dimensional QKD with time-bin encoding, which can be implemented using a standard commercial QKD system without any hardware modifications. Instead, we show that the eavesdropper’s information (Eve) can be bounded by simply randomizing the time-bins order of the qudits sent by the transmitter (Alice). Our approach is particularly relevant for systems in the detector saturation regime, where the secure key rate is limited by the number of photons that can be detected by the receiver. The detector saturation regime is the common regime among the deployed systems35.
We further analyze the expected secure key rate. We introduce two security analyses against two standard types of attacks; individual attacks, where the eavesdropper is limited to interact with each time-bin separately and independently, and coherent attacks, which are the most powerful class of attacks. The analysis of individual attacks provides an upper bound for the secure key rate, assuming a realistic attack with currently available technologies. The lower bound of the secure key rate is obtained by generalizing the analysis in ref. 37 which employs a numerical method to provide optimized key rates for two-dimensional systems, to higher dimensions. The complete open-source package used in this work is available online38.
We experimentally demonstrate a 32-dimensional protocol over a 40 km long fiber using a standard coherent one-way (COW) QKD system that requires only two single-photon detectors and one interferometer at the receiver end. We show that our new high-dimensional protocol yields a twofold increase in the asymptotically secure key rate for individual attacks, compared to the two-dimensional COW protocol, using the exact same experimental setup.
Results
Protocol scheme
Traditionally, high-dimensional QKD protocols have relied on the utilization of multiple optical modes to encode quantum states that belong to a set of two mutually unbiased bases8,9. By measuring the error rates associated with these bases, the extent of information that Eve might possess can be limited as her actions must maintain the measured error rates. To measure the error rates in the two mutually unbiased bases, Bob typically employs a multi-port interferometer, often employing a discrete Fourier transform (DFT), followed by multiple single-photon detectors.
In our proposed protocol, we impose limitations on the information accessible to Eve by evaluating the error rate associated with a basis defined by a set of multiple modes, together with the visibility of interference between their nearest neighbors, as depicted in Fig. 1. The visibility measurements are conveniently obtained by employing a two-port Hadamard (H) transformation. To further restrict Eve’s potential access to information, Alice randomizes the ordering of the modes using a permutation σ. Consequently, any transformation applied by Eve must preserve the relative phase between these modes. Although these constraints on Eve’s actions may not be as strong as the DFT measurement, they suffice, as we show below, to limit Eve’s potential knowledge.
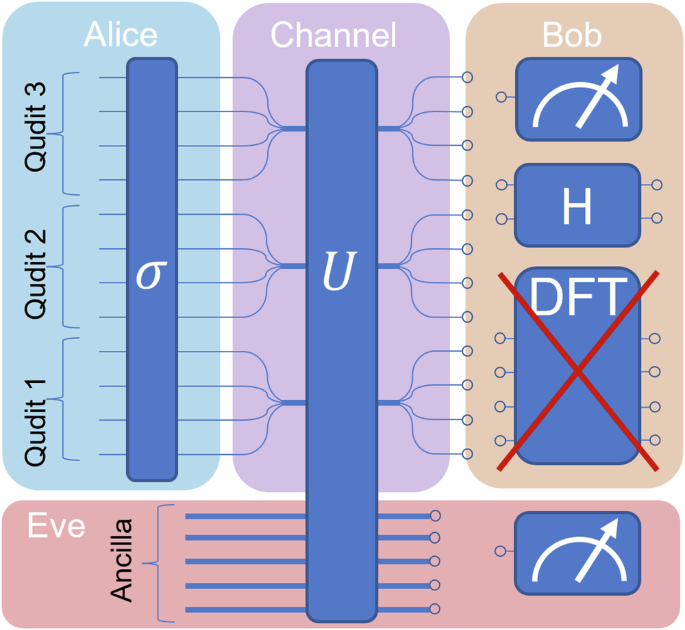
Alice encodes three 4-dimensional qudits, represented here using 12 dual-rail optical modes, and applies a secret random permutation (σ). See the complete protocol steps in the main text. Bob is restricted to measuring the photon occupation in each mode and applying a Hadamard (H) transformation. Importantly, since Bob does not use a discrete Fourier transform (DFT) measurement, he can use a standard two-dimensional system with a two-port interferometer. Eve attacks the quantum channel by applying a nonlocal unitary transformation U. The transformation U operates on a Hilbert space containing the encoded qudits space and an arbitrary-dimension ancilla qudits space, while σ, H, and DFT operate on the optical modes space.
Importantly, the key features of the described protocol do not depend on the specific set of optical modes or on the particular photonic degrees of freedom that are used for encoding the qudits. Moreover, they are equally applicable for implementations based on weak coherent pulses, single-photon states, or entangled photon pairs. In this work, we focus on analyzing the new protocol using time-bin encoding with weak coherent pulses, in a configuration that generalizes the widely used COW protocol.
High-dimensional coherent one-way protocol
In the COW protocol, the bit string is encoded by the time of arrival of weak coherent laser pulses, and channel disturbance is monitored by measuring the visibility of the interference between neighboring pulses39. That is, bits 0 and 1 are sent using (leftvert alpha rightrangle leftvert 0rightrangle) and (leftvert 0rightrangle leftvert alpha rightrangle), respectively, where (leftvert 0rightrangle) is the vacuum state and (leftvert alpha rightrangle) is a coherent state. The receiver (Bob) simply recovers the bit value by measuring the arrival time of the laser pulse. This time-bin encoding avoids the potential ambiguity of on-off keying, where all four combinations of occupied and empty time-bins are employed to transmit the key value. To detect attacks, a small fraction of the pulses are split to a monitoring line by a fiber beam splitter. In the monitoring line, Bob checks for phase coherence between any two successive laser pulses using an imbalanced interferometer and one SPD19,40,41,42,43,44,45,46,47.
In our high-dimensional protocol, Alice encodes a sequence of time-bins which are occupied with probability 1/d and empty with probability 1−1/d. Alice gathers m frames of size d time-bins to packets of m ⋅ d time-bins and transmits the packets with an empty time-bin that separates them. Including empty time-bins between packets allows us to apply the de Finetti theorem as explained in the security analysis in Section “Security analysis”. Although adding an empty time-bin decreases the transmission rate of information in the channel, in the saturated detectors regime this effect is negligible. Therefore, adding empty time-bins is an established technique in time-bin QKD protocols48,49,50. After Bob detects enough photons to accurately estimate the error rate and visibility, they start the classical post-processing.
Due to the low occupation of the time-bins and the long dead time of the detectors, many packets are not detected at Bob’s side and we discard them. For each detected photon, Bob announces the frame index that triggered the detection within the packet, i ∈ {1…m}. Then, without an optional permutation step, we extract a key if only one time bin is occupied in the frame, and discard the packet otherwise. We define the sifting success rate as the probability that a detected photon is not discarded. This sifting process ensures a set of orthogonal, distinguishable, states that define the key value. States with multiple occupied time bins may serve for security analysis.
To enhance the sifting success rate, Alice can rearrange the time-bin order within the packet using a permutation. Formally, let t0, …, tmd−1 ∈ {0, 1} be the packet that Alice sends. After Bob’s measurements, Alice announces on a public channel a permutation σ of the d ⋅ m time-bins such that the permuted packet tσ(0)…tσ(md−1) induces a new division of the m ⋅ d time-bin packet to m frames of size d that maximizes the number of frames that yields a key, namely frames that consist of only one occupied pulse. Bob then announces over the public channel the frame index that triggered a photon detection to generate a sifted key with Alice.
Due to our encoding scheme, the number of occupied time-bins in each packet is binomially distributed with a success rate of 1/d and m ⋅ d independent experiments. Thus, each packet consists of m occupied pulses on average. To estimate the sifting failure rate for m ≫ 1, we obtain using the Chernoff bound, that Alice can discard (ksqrt{m}) pulses to remain with a packet with a sifting success probability of 1, with a failure probability that decays exponentially with k. We analyze the sifting success probability for finite d and m in the Supplementary Information, Section 1, showing that the sifting success probability increases with m for any d.
In contrast to the role of permutations in our protocol, they are often used in QKD protocols to ensure a more uniform distribution of errors or to analyze the security of keys extracted from N-partite states, as in advantage distillation methods51,52. By symmetrizing the state through permutations, it becomes possible to approximate the state as a mixture of i.i.d. (independent, identically distributed) states, thereby simplifying security proofs.
In two-dimensional COW protocols, the security stems from testing the coherence between successive pulses in Bob’s monitoring line. In principle, in high-dimensional COW protocols, testing the phase coherence only between successive pulses is insufficient, because standard security proofs for high-dimensional QKD protocols require testing the phase coherence of multiple time-bins. Nevertheless, in our encoding scheme, any two successive time-bins can be occupied with pulses, and we measure their coherence. Eve, therefore, must preserve the relative phase between any two successive pulses. As we show below, this is sufficient for quantifying the amount of information Eve can extract, allowing us to set bounds on the secure key rate.
The number of bits in the sifted key, per detector dead time, is log2(d). High-dimensional encoding, therefore, has a clear advantage in the detector-saturated regime. However, the amount of information that is revealed to an eavesdropper can also increase with the dimension d and the frames within the packet m. The security proof of the protocol, presented in Section “Discussion”, thus relies on finding the optimal dimension parameters that maximize the final secure key rate. Furthermore, The permutation enhances sifting but may require estimating the coherence between pulses that are far apart. However, the standard hardware of COW can only test the coherence of successive pulses. Therefore, the ability to estimate the coherence between distant pulses decreases with their distance. This effect does not play a role in our upper bound analysis, however, it decreases the secure key rate in our lower bound analyses as we show in Section “Security analysis”.
The protocol steps are outlined below:
-
1.
Encoding by Alice: Alice encodes information by sending packets containing m ⋅ d time-bins, separated by an empty time-bin. Each packet consists of m frames, with each frame containing d time-bins. Within a frame, each time-bin is occupied with probability (frac{1}{d}) or left empty with probability (1-frac{1}{d}). This encoding scheme results in an average of m occupied time-bins per packet.
-
2.
Detection by Bob: Bob splits the incoming pulses into two lines:
-
(i)
A data line, where a single-photon detector measures the arrival times of photons.
-
(ii)
A monitoring line, where an imbalanced interferometer measures the relative phase coherence between successive pulses.
-
(i)
-
3.
Post-Processing: After Bob detects a sufficient number of photons to estimate the visibility (see Supplementary Information, Section 2), the classical post-processing begins:
-
(i)
Permutation: To enhance the sifting success rate, Alice may optionally apply a permutation to the time-bin order within the packet. The permutation maximizes the number of frames that yield a key.
-
(ii)
Frame Selection: For each detected photon, Bob announces the frame index that triggered a detection within the packet (i ∈ {1, …, m}).
-
(iii)
Sifted Key Extraction: Alice and Bob extract a key bit only from frames with exactly one occupied time-bin. Frames with multiple or no occupied time-bins are discarded. The time-bin index of the detected photon within a successfully sifted frame corresponds to the raw key bits. This results in ({log }_{2}(d)) bits per detected photon for frames that pass the sifting process.
-
(iv)
Error Correction and Privacy Amplification: Alice and Bob apply error correction to reconcile their key estimate QBER. Bob also announces the arrival times at the monitoring line to calculate visibility, which is used to monitor potential eavesdropping. Finally, privacy amplification is applied to ensure the final key is information-theoretically secure.
-
(i)
Security analysis
Our high-dimensional security analysis is based on the analytical framework developed for the standard two-dimensional COW protocol. An upper bound on the secure key rate of the two-dimensional COW protocols was derived by analyzing individual attacks53. The upper bound was found to scale linearly with the transmittance of the channel. Later, lower bounds on the secure key rate against general attacks have been derived, showing quadratic scaling37. However, so far, all COW-QKD systems19,40,41,42,43,44,45,46,47, still employ the original security proof53 since it is the most realistic attack with current technologies. More recently, zero-error attacks, eavesdropping without breaking the coherence between adjacent non-vacuum pulses, have also been studied for the COW protocol54,55,56. These attacks require an extremely low number of detected photons and are thus irrelevant to the detector-saturated regime that we consider in this work.
In this section, we present two security analyses against two classes of attacks, setting an upper bound and a lower bound on the secure key rate. The purpose of presenting the upper bound is threefold. First, to compare with other experimental works that often analyze an upper bound of the secure key rate19,41,43,44,46. Secondly, unlike the lower bound analysis that applies to the most general attack by Eve, the attack assumed for the upper bound can be implemented by attacking single time-bins, an attack that might be possible even with current technology. Finally, a comparison between the upper and lower bounds enables to estimate their tightness. In this section, we analyze the security against individual and coherent attacks under the asymptotic analysis assumption that refers to the infinite post-processing block size. For an analysis of finite block effects, see the Supplementary Information, Section 2. Also, in both classes of attacks, individual and coherent, we assumed that the occupation of the state is low so that the advantage of photon number-splitting attacks is negligible. This assumption is less accurate for individual attacks, where the optimal occupation is rather high. We, therefore, present in the Supplementary Information, Section 4, the secure key rate bounds that take into account the photon number-splitting attack, and discuss the decoy-state method to overcome such an attack.
Secure key rate upper bound
To calculate the upper bound of the secure key rate for individual attacks, we focus on Eve’s action on a single time-bin. It can be defined by a linear transformation describing the action on non-occupied (vacuum) and occupied (coherent state) time-bins ({vert 0rangle }_{A},{vert sqrt{mu }rangle }_{A}):
where ({vert {v}_{j}rangle }_{E}(jin {0,mu })) are the states that Eve attaches to the vacuum part of the signal, while ({vert {p}_{mu }rangle }_{E}) is the state that Eve attaches to the photon part of the signal. We assume μt ≪ 1 so that we can neglect multiphoton terms. Here we assume that Eve’s states can be arbitrary and conditioned to some constraints described in the following. The probability amplitude of each of the terms guarantees that Eve’s attack does not increase the quantum bit error rate Q (QBER) of the channel, i.e., the probability that Bob receives a wrong bit value.
Coherence between occupied time-bins is monitored by analyzing the detection events in the monitoring line. The phase delay between the two arms of the interferometer in the monitoring line is chosen such that two successive non-empty pulses sent by Alice will interfere destructively in one output port and constructively in the other port. We quantify the degree of coherence by the visibility:
where P(Dc) and P(Dd) are the probabilities to measure a photon at the constructive and destructive ports, respectively. Since Eve’s attack should conserve visibility, we can derive a constraint on Eve’s action on two successive pulses sent by Alice (leftvert sqrt{mu }rightrangle leftvert sqrt{mu }rightrangle). Assuming μt ≪ 1, Eve’s action is given by:
The visibility constraint then yields (see Methods, “Detailed secure key rate upper bound analysis”):
The last constraint on Eve’s transformation is that it must be unitary. Thus in the μt ≪ 1 limit we get from Eq. (1):
Our security analysis is therefore based on three constraints imposed on Eve’s action: (i) It must retain the QBER (Eq. (1)), (ii) it must conserve the visibility (Eq. (4)), and (iii) it must be unitary (Eq. (5)).
To compute the amount of information that can be extracted by Eve, as quantified by the Holevo information57, we first need to analyze her action on a qudit with occupation μ(i) in the ith time-bin. Neglecting all multi-photon terms, Eve’s action can be presented by:
where (vert {V}_{i}rangle ={vert {v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E}) is Eve’s state representing the case where she sends a vacuum state at time-bin (i,vert {C}_{i}rangle ={vert {v}_{0},ldots ,{v}_{0},{p}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E}) is Eve’s state representing the case where she sends to Bob a photon at the right time-bin i, and (vert {W}_{i,k}rangle ={vert {v}_{0},ldots ,{v}_{0},{p}_{0}^{(k)},{v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E}) is Eve’s state representing the case where she sends to Bob a photon at the wrong time-bin k.
Next, we compute the density matrices of Eve’s subsystem, conditioned by the event where Alice sends a pulse at time-bin i and Bob detects a photon at some arbitrary time-bin:
Similarly, the density matrix of Eve’s subsystem is conditioned by the event where Bob detects a pulse at time-bin i and Alice sent the pulse at an arbitrary time-bin:
Knowing these density matrices, we can apply the Devetak–Winter bound for the secure key rate by calculating the Holevo information58. The Holevo information on Alice–Eve channel χAE and on Bob–Eve channel χBE, are defined by:
where (Cin {A,B},S(rho )=-Tr(rho {log }_{2}rho )) is the von Neumann entropy of ρ. The maximal information Eve can extract is bounded by the maximum of these two quantities. Direct computation of Eq. (9) shows that χBE > χAE (see Methods, “Detailed secure key rate upper bound analysis”), so from this point on, we will focus on analyzing χBE.
Eve has no constraints over (leftvert {p}_{0}rightrangle) as it does not affect the three constraints imposed by Eqs. (1), (4), and (5). Thus, in order to maximize her information, she can choose (leftvert {p}_{0}rightrangle) which is orthogonal to all other vectors (vert{v}_{0}rangle ,vert {v}_{mu }rangle ,vert {p}_{mu }rangle). Conveniently, we can then separate the trace of the above matrices to a trace of density matrices that contain only one (leftvert {p}_{0}rightrangle) in time-bin i for i = 1…d, and a trace of matrices that do not contain (leftvert {p}_{0}rightrangle), yielding (see Methods, “Detailed secure key rate upper bound analysis”):
where we define (vert {W}_{i}^{{prime} }rangle ={{d-1,terms}atop{{overbrace{vert {v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }}}}), so that (vert {W}_{i}^{{prime} }rangle otimes vert {p}_{0}rangle =vert {W}_{i,d}rangle) and (vert {W}_{i,j}rangle) are equivalent up to reordering the order of the time-bins.
After diagonalizing the density matrices and computing the traces, we obtained the following expression for the Holevo information (see Methods “Detailed secure key rate upper bound analysis”):
To maximize χBE, we can minimize 〈v0∣pμ〉 under the constraints imposed by Eqs. (4) and (5). Using a parametric representation of (vert {v}_{0}rangle ,vert {p}_{u}rangle) and (vert {v}_{u}rangle) in 3-D space, we find that the maximal information Eve can extract (max {{chi }_{BE}}) is obtained for:
An upper bound on the secure key fraction can now be computed, using the bound53.
We compare the secure key rates and analyze the resilience to noise in Supplementary Information, Section 6. We find that while increasing the dimensional encoding might increase the secure key rate for low error rates, the resilience to noise does not improve with dimensional encoding.
Although analyses for two-dimensional QKD protocols have been introduced by Devetak–Winter bound53, the generalization of the analytical methods for high-dimensional protocols is difficult due to the challenge of diagonalization of the density matrices representing the states. In our analysis, we solve this issue by choosing the natural basis that divides the state’s space into orthogonal subspaces. By that, we extract an analytical formula for the secure key rate upper bound (13).
Secure key rate lower bound
To analyze the security of the protocol against general coherent attacks in the asymptotic limit, we extend the method proposed by Moroder et al.37 for high-dimensional encoding, which employs a numerical method to provide optimized key rates59,60,61,62.
For completeness, in this chapter we present the security analysis derived in ref. 37, with the necessary adaptation for high-dimensional encoding. The adaptation includes using the generalized secure rate formula for high dimensions, the generalized high-dimensional positive operator value measurements, and the sifting maps acting on high-dimensional states. In addition, the conversion from infinite dimensional space representing coherent states to a finite dimension that can be numerically simulated has also been generalized to high-dimensional encoding in this work. Here we choose to avoid adding the coherence measurement of the first and the last time-bins in the packet as a constraint on Eve because it is not measured, even in the two-dimensional COW protocol. Removing this constraint has a dramatic consequence on the information Eve can produce primarily due to the allowance of a small phase shift between adjacent pulses, which accumulates to create a substantial phase shift between the first and last pulses within the packet. Lastly, we have considered the detectors’ dead time, resulting in the detectors entering a saturation regime. The complete open-source Matlab package used in this work is available online38.
General attacks often do not have an advantage over collective attacks when the de Finetti theorem applies63. The theorem holds when the quantum state shared by Alice and Bob is composed of sequences and the state itself is invariant under permutations of the sequences’ order. The challenge in directly applying the de Finetti theorem to COW is that the protocol induces a fixed ordering of the signals by coherent measurements between successive time bins. Therefore, the state is not invariant under the permutation of the signals. This issue can be solved by grouping time-bins into sequences of size m ⋅ d, which we call packets, separated by an empty time-bin. The complete protocol is invariant under permutations of the order of the packets. Therefore, security against collective attacks for a packet implies security against coherent attacks for the packet sequence. We emphasize that although adding an empty time-bin decreases the transmission rate of information in the channel, in the regime of a large detector dead time this effect is negligible.
Secure key rate formula: Here we assume that the shared state between Alice, Bob, and Eve has an i.i.d. (independent, identically distributed) structure of packets. We can therefore analyze the state ρABE associated with a single packet. Alice and Bob generate a sifted key based on a public announcement denoted by v. This generation process can be presented using maps ({Lambda }_{v}^{A}otimes {Lambda }_{v}^{B}). These maps are often called a filter or squashing operation64,65. Specifically, ({Lambda }_{v}^{B}) transforms any incoming state to a finite-dimensional output state; see Methods, “Detailed secure key rate lower bound analysis” for more information. The three parties share the state ({sigma }_{bar{A}bar{B}E}) which is determined by ({Lambda }_{v}^{A}otimes {Lambda }_{v}^{B}({rho }_{ABE})=p(v){sigma }_{bar{A}bar{B}E}), where announcement v occurs with a probability of p(v), and (bar{A}) and (bar{B}) represent the output spaces, which serve as logical qudits.
Using the secure key rate lower bound obtained by Berta et al.66 (To derive the secure key rate bound, Berta et al. rely on the secure key rate bouned obtained by Devateck and Winter58 and entropic uncertainty relations), for each announcement we obtain a secure key rate lower bound ({log }_{2}(d)-{h}_{d}({e}_{v})-{h}_{d}({delta }_{v})), where ({h}_{d}(x)=-xlog frac{x}{d-1}-(1-x)log (1-x)) represents the d-dimensional entropy, see Methods, “Secure key rate formula derivation”. Here, ev represents the bit error rate, and δv represents the phase error rate that would be obtained if both Bob and Alice were measured in a mutually unbiased basis. This lower bound can be estimated directly by observable quantities. However, in our protocol, we do not measure directly δv. Therefore, the estimation of δv is essential for establishing an upper bound on Eve’s knowledge of the sifted key. In practice, it is often more convenient to consider the averaged value of conclusive announcements v ∈ Vc and the total probability of a conclusive measurement (G={sum }_{vin {V}_{c}}p(v)le 1). The secure key rate lower bound per packet is obtained:
In order to bound the value of Rm from below, we utilized the concavity property of hd and expressed it in terms of the average error rates ({bar{e}}_{c}={sum }_{vin {V}_{c}}p(v){e}_{v}/G) and (bar{delta }={sum }_{vin {V}_{c}}p(v){delta }_{v}/G). It is important to note that ({bar{e}}_{c}) and G are observable quantities, whereas (bar{delta }) is not measured directly in our protocol. Therefore, we estimate ({bar{delta }}^{max}), which represents the largest phase error that satisfies all other constraints. To maximize the function hd within the range [0, 1 − 1/d], we can search for the maximum value of ({bar{delta }}^{max}), as hd is a monotonically increasing function in this range.
Phase error estimation: A significant difficulty in calculating Eq. (14) lies in the establishment of an upper limit for the average phase error, denoted as (bar{delta }). This parameter can be expressed as the expectation value on the original bipartite state ρAB = trE(ρABE), utilizing the maps ({Lambda }_{v}^{A}otimes {Lambda }_{v}^{B}):
The operators ({F}_{{delta }_{v}}) represent the corresponding phase error operators, see Methods, “Detailed secure key rate lower bound analysis”.
When Alice and Bob possess partial knowledge about the state ρAB, it can be represented as known expectation values ki = tr(ρABKi) for specific operators Ki, which are constructed using local projection measurements at the sites of Alice and Bob. In Methods, “Measurement description”, we define the set Ki. To calculate the outcome probabilities ki, we evaluate (tr({widetilde{rho }}_{AB}{K}_{i})={k}_{i}), where ({widetilde{rho }}_{AB}) represents the bipartite state of Alice and Bob without an eavesdropper, but accounting for the losses and errors resulting from channel imperfections (see Methods “Channel loss” and “Error model”).
To find the maximum phase error ({bar{delta }}^{max}) under the constraints, we define the semidefinite program:
The convex optimization problem can be efficiently solved using standard numerical tools, enabling us to obtain the precise optimal value of ({bar{delta }}^{max}). It is worth noting that optimizing the linear objective (bar{delta }) rather than ({sum }_{vin {V}_{c}}p(v)[{h}_{d}({delta }_{v})]) enables the formulation of a linear optimization problem. However, this approach does not provide a tighter lower bound. Specifically, the lower bound obtained through the linear problem will be less tight for higher dimensions.
Numerical secure key rate bounds
First, we study the lower bound of the asymptotic secure key rate, using Eq. (14). Finite block effects are analyzed in the Supplementary Information, Section 2. For a given total system loss, including channel losses and Bob’s finite detection efficiency, we look for the optimal occupation of the signal μ that maximizes the lower bound. As expected, we find that our high-dimensional encoding decreases the secure key per detected photon, which exhibits a quadratic decrease with the loss for any dimensional encoding size; see Supplementary Information, Section 7. The secure key rate, however, increase with the dimensionality up to an optimal dimension (see Methods “Detailed photon detection rate analysis”). For example, with parameters corresponding to a typical system: dark count rate of 5 ⋅ 10−8, bit error rate of 0.5%, visibility of 99.5%, dead time of 10 μs, and pulse duration of 2ns, the optimal secure key per second is achieved for d = 3 in the range of loss up to 6 dB (Fig. 2).
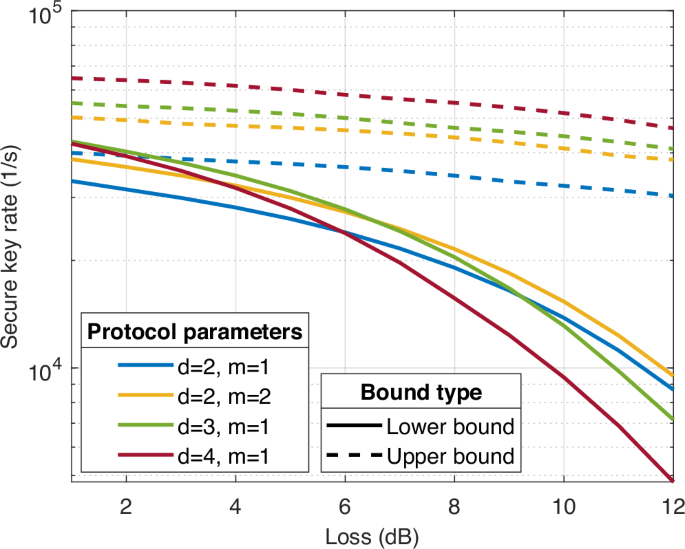
The lower and upper bounds on the secure key rate on a logarithmic scale are presented as a function of the system loss. Different colors represent different encoding parameters where d is the dimension and m is the number of frames within a packet. Solid lines present the lower bound obtained by the numerical optimization of Eq. (14), while the dashed lines present the upper bound obtained by Eq. (13). A finite secure key rate lower bound is achieved for all cases, indicating that the protocol is secure. The optimal lower bound secure key rate is achieved for d = 3, m = 1 in the range of up to 6dB loss. In lower losses, the secure key rate is maximized for d = 2, m = 2. Here Bob’s detector dark count rate is 5 ⋅ 10−8, bit error rate of 0.5%, visibility of 99.5%, dead time of 10 μs, and a pulse duration of 2 ns.
To estimate the tightness of the lower bound found by the numerical optimization, we compare it to the upper bound, which is computed by multiplying the number of secure bits per photon calculated using Eq. (13) by the number of photons per second. The obtained curves depicted in Fig. 2 show that both bounds are of the same order of magnitude. Note that both the upper bound and the lower bound are calculated assuming an empty time-bin between packets of m ⋅ d time-bins. In the detector saturation regime, the additional time-bin hardly changes the secure key rate. Here we set a realistic detector dead time of 10 μs, a pulse duration of 2 ns, and obtained a saturation in the detection rate at the optimized occupation, as typically happens in real-life scenarios. In addition, we present the secure key rate outside the detector saturation regime in the Supplementary Information, Section 3.
Experimental Implementation
The important feature of our high-dimensional protocol is that it can be implemented in a standard two-dimensional COW system, illustrated in Fig. 3, without any hardware changes. The system consists of a transmitter (Alice) and a receiver (Bob). The transmitter sends a train of weak coherent pulses that are prepared from a continuous wave (CW) laser emitting at λ = 1550 nm, by an intensity modulator (IM) running at 500 MHz. Before leaving the transmitter, the pulses are attenuated to reach a single photon energy level using a variable optical attenuator (VOA). To generate 200 ps long pulses with random occupations of τ = 2 ns time-bins we use a field programmable gate array (FPGA). Synchronization is achieved over the 40 km fiber channel using the White Rabbit protocol67. To interfere two successive pulses at the receiver’s end, an unbalanced fiber-interferometer is installed, where we use Faraday mirrors to compensate for random polarization drifts in the fiber (Fig. 3). We use single-photon avalanche detectors (SPADs) with 20% detection efficiency and 400 ps timing resolution. The detectors’ dead time is 4 μs, limiting the maximal raw key rate to 250 kHz.
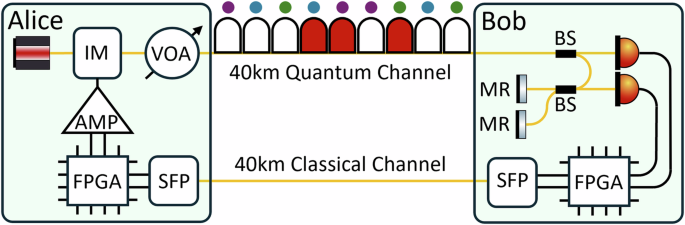
Alice’s transmitter (left) consists of a continuous wave (CW) telecom laser at λ = 1550 nm that is modulated using an electro-optic intensity modulator (IM) running at 500 MHz. The IM is fed by radio frequency (RF) signals generated by a field-programmable gate array (FPGA) and amplified by an RF amplifier (AMP). The optical pulses are passed through a variable optical attenuator (VOA) that regulates the mean photon number per pulse. The weak coherent pulses are delivered to Bob’s end through a 40 km long single-mode fiber (SMF-28). Our post-processing step divides the nine time-bin sequences into three frames represented by the colored spots, where each consists of one occupied time-bin. Bob’s receiver (right) consists of an asymmetric beamsplitter (BS), which provides a passive choice of the measurement basis; 90% of the photons travel directly to the data detector, and 10% pass through an unbalanced interferometer made of two faraday mirrors (MR) and are detected by the monitor detector. We lock the laser’s wavelength to the interferometer so that the monitor detector always measures the dark port of the interferometer. The interference visibility is estimated by registering the detection events due to the interfering and non-interfering events. In addition to the 40 km long quantum channel that delivers the weak coherent pulses, we use a separate 40 km SMF-28 fiber and small form-factor pluggables (SFP) for all classical communication between Alice and Bob and to distribute an optical clock signal between them based on the White Rabbit protocol67. State preparation and sifting are run by two FPGAs at Alice’s and Bob’s ends.
We analyze the protocol’s performance for different dimensions and compare the experimental results with the predictions of a cleaner theoretical model. The model assumes that the bit error rate scales linearly with the dimensionality and that the visibility is independent of the dimensionality. The reason behind this choice is that the bit error rate increases with the total dark count probability, which scales linearly with the number of time bins, namely the dimension. In contrast, visibility measurement is a result of interference of pulses occupying two successive time bins, which is independent of the rest of the time bins. We show experimentally that the visibility does not depend on the dimension in the Supplementary Information, Section 7.
We present the secure key rate in Fig. 4, obtained by multiplying the raw bits per photon by the number of detected photons per second (see Supplementary Information, Section 7). It is evident that in the upper bound analysis, for d = 2 we obtain a maximal secure key rate of 7.6 ⋅ 104s−1, for an occupation of μ = 0.07. Keeping the same occupation, at d = 8 we almost double the secure key rate, obtaining a rate of 1.4 ⋅ 105s−1. A higher secure key rate is achieved in d = 8 for an occupation of μ = 0.175, however, the high occupation opens the door to photon number splitting attacks, see Supplementary Information, Section 3. Increasing the dimensionality reduces the occupied time-bins per second and therefore enables higher occupation μ before saturating Bob’s detectors. Therefore, the detector’s saturation is obtained at higher occupations for higher dimensions, and the optimal occupation that maximizes the secure key rate increases with the dimension, see more details in Supplementary Information, Section 7.
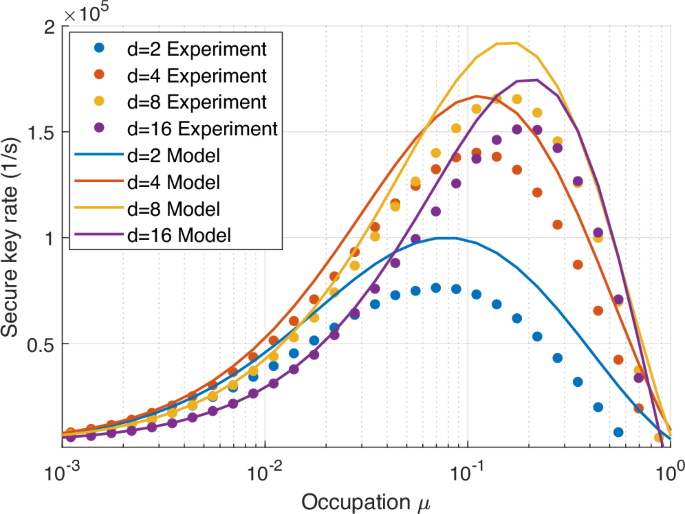
The secure key rate is obtained by multiplying the secure bits per photon by the number of measured photons per second. The secure bits per photon is obtained by measuring the bit error rate, visibility, and loss, and applying the upper bound on the secure key rate found in Eq. (13). Dots represent the results obtained experimentally, and solid lines represent our model system. The model assumes the bit error rate scales linearly with the dimensionality, and the visibility is independent of the dimensionality, as explained in the main text. Under the simplified attack assumed for the upper bound analysis, the optimized secure key rate depends on the dimension, see discussion in the main text. Here, we use second-long packets (i.e., m ~ 108), constrained by the FPGA memory. Increasing m maximizes the secure key rate because individual attacks are independent of m, and the sifting success probability asymptotically approaches one, see Supplementary Information, Section 1.
Although the experimental results and theoretical model exhibit similar trends, the model fails to capture the exact secure key rate, due to the oversimplification of the model, which assumes linear scaling of the QBER with the dimension size. For a description of the noise sources, the QBER, and visibility measurements as a function of the dimension, see the Supplementary Information, Fig. S.8.
Discussion
Using our scheme for high-dimensional QKD that leverages standard commercial hardware, we managed to enhance the secure key rate, showcasing the effectiveness of our method. However, the potential applicability and implications of our research go far beyond our system.
First, our technique has the potential to be integrated with other time-bin QKD systems. Although we showed enhancement in the secure key rate for the most popular and cost-effective commercial design based on the standard single-photon avalanche photodiode, a similar analysis also showed improvement for high-end QKD systems based on superconducting nanowire detectors. For example, considering detector dead time of 10 ns and modulation rates as high as 10 Gbps, the secure key rate in dimension d = 8 may increase by a factor of 2 compared to standard two-dimensional COW encoding. In general, for time-bins systems, our approach for encoding high-dimensional information enables higher key rates in the detector’s saturation regime. This regime is obtained in typical systems up to 100 km of fiber links35.
Moreover, our high-dimensional QKD method is not limited to time-bin encoding and is directly applicable to other QKD qudit encoding schemes, such as in the spatial14,15,68,69,70,71,72,73,74,75, and spectral76,77 degrees of freedom. For example, QKD with states encoded with spatial modes such as non-overlapping Gaussian beams, orbital angular momentum, or waveguide modes requires a multiport interferometer. Our approach may offer new opportunities for the implementation of high-dimensional QKD with spatial encoding relying on a single Michelson interferometer. Similarly, applying our protocol in the spectral domain using frequency-bins and a single electro-optic modulator to interfere adjacent spectral modes can pave the way for high-dimensional QKD with frequency-bins. This suggests that our method could serve as a more generalized solution for high-dimensional QKD, applicable across diverse platforms and systems.
Lastly, it is worth noting the potential of our approach to apply to systems working with entangled photon pairs, in addition to weak coherent states. The adaptability of our method could further secure communication in systems exploiting entangled states with different degrees of freedom of encoding, including time-energy78,79,80,81,82, angle-angular momentum70,83,84,85,86, and position-momentum87,88,89,90,91.
Therefore, our research on high-dimensional COW QKD by interfering just neighboring modes and leveraging commercially available hardware not only enhances secure key rates but also holds broad applicability across various QKD schemes, making high-dimensional QKD practical for widespread use.
Methods
Detailed secure key rate upper bound analysis
As a reminder, we can look at Eve’s action as a linear transformation53:
where Q is the QBER i.e., the probability that Bob accepts the wrong bit value. μ and t are the pulse occupation and the link transmission. These amplitudes of the states are chosen so that Eve does not change the QBER of the data line.
The loss of coherence is monitored by analyzing the detection events in the monitoring line. The phase between the two arms of the interferometer in the monitoring line is chosen such that two successive non-empty pulses sent by Alice will interfere destructively in one output port and constructively in the other port. We label the probability of detecting a photon in the constructive port by P(Dc) and the probability of detecting a photon at the destructive port by P(Dd). The loss of coherence by Eve’s attack is measured by the visibility:
Assuming μt ≪ 1 we can neglect the two-photon terms. Eve’s action on a successive pair of occupied pulses (vert sqrt{mu }rangle vert sqrt{mu }rangle) is then given by:
The action of the interferometer at Bob’s end yields:
where we define the constructive and destructive output modes of the interferometer by ({vert {D}_{c/d}rangle }_{B}=frac{1}{sqrt{2}}({vert 1,0rangle }_{B}pm {vert 0,1rangle }_{B})). The probability that the photon is detected at the constructive/destructive detector is thus given by (P({D}_{c/d})propto | ({vert {p}_{mu },{v}_{mu }rangle }_{E}pm {vert {v}_{mu },{p}_{mu }rangle }_{E}){| }^{2}). The visibility constraint on Eve’s action is therefore given by:
The third constraint on Eve’s transformation is that it must be unitary. In the μt ≪ 1 limit we get
To compute the amount of information that can be extracted by Eve, quantified by Holevo information, we first need to analyze her action on a qudit with occupation μ(i) in the ith time-bin. Neglecting all multiple photon terms, Eve’s action can be presented by:
where (vert {V}_{i}rangle ={vert {v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E}) is Eve’s state representing the case where she sends a vacuum state at time-bin (i,vert {C}_{i}rangle ={vert {v}_{0},ldots ,{v}_{0},{p}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E}) is Eve’s state representing the case where she sends to Bob a photon at the right time-bin i, and (vert {W}_{i,k}rangle ={vert {v}_{0},ldots ,{v}_{0},{p}_{0}^{(k)},{v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E}) is Eve’s state representing the case where she sends to Bob a photon at the wrong time-bin k.
The density matrix representing Eve’s subsystem, conditioned on the event where Alice transmits a pulse at time-bin i and Bob detects a photon at any arbitrary time-bin, can be expressed as follows:
The density matrix of Eve’s subsystem is conditioned by the event where Bob detects a pulse at time-bin i and Alice sends the pulse at an arbitrary time-bin:
Eve’s information is bounded by the Holevo bound on the Alice–Eve channel (χAE) and on the Bob–Eve channel (χBE). The maximum amount of information Eve can extract is given by (max {{chi }_{BE},{chi }_{AE}}). We start by analyzing χBE, and then we show that χBE > χAE.
As explained in the main text, Eve can choose the ({vert {p}_{0}rangle }_{E}) state to be orthogonal to all other states. We now use this to simplify Eve’s Holevo information. We start by choosing an orthonormal set of states ({G}^{{prime} }) that span the space that describes Eve’s system for a single time-bin, where ({vert {p}_{0}rangle }_{E}in {G}^{prime}) is one of the states in the set. The basis for Eve’s system that spans a d-dimension qudit is simply the tensor product of this basis, i.e. ({vert {v}_{1},ldots ,{v}_{d}rangle }_{E}in G={vert {v}_{1}rangle }_{E}otimes ldots otimes {vert {v}_{d}rangle }_{E}in mathop{prod }nolimits_{i = 1}^{d}{G}^{{prime} }).
We can now split the space G to d+2 groups: Gi, i = 1…d will consist of states with ({leftvert {p}_{0}rightrangle }_{E}) in the ith time-bin, and other vectors from ({G}^{{prime} }) in the rest of the time-bins. Gd+1 will consist states without ({vert {p}_{0}rangle }_{E}) at any time-bin, and Gd+2 will consist states ({vert {p}_{0}rangle }_{E}) in more than one time-bin. We further define ({P}_{l}={sum }_{leftvert vrightrangle in {G}_{l}}leftvert vrightrangle leftlangle vrightvert) and since ∑Pl = I, we can express χBE by:
We can simplify this expression using the fact that the von-Neumann entropy of a block-diagonal matrix equals the sum of the entropies of the blocks along the diagonal. We claim that the matrices that appear in Eq. (26) are all block-diagonal, by the construction of the sets Gi. To show this, it suffices to prove that E ({langle v| {rho }_{E}^{A = k}| urangle }_{E}=0) for every k and every ({vert vrangle }_{E}in {G}_{i},{vert urangle }_{E},in ,{G}_{j},j,ne ,i). Since each density matrix is by itself a sum of density matrices of pure states, we are left with proving that E〈v∣φ〉〈φ∣u〉E = 0 for every state ({vert varphi rangle }_{E}) describing Eve’s system after a qudit was sent by Alice and received by Bob, represented by (leftvert {C}_{i}rightrangle ={leftvert {v}_{0},ldots ,{v}_{0},{p}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rightrangle }_{E},iin 1ldots d) or (vert {W}_{i,k}rangle ={vert {v}_{0},ldots ,{v}_{0},{p}_{0}^{(k)},{v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E},i,ne, kin 1ldots d). It is easy to verify by inspection that ({atop {E}}langle v| {C}_{i}rangle {langle {C}_{i}| urangle }_{E}=0) if ({vert vrangle }_{E}) or ({vert urangle }_{E}) are not both in Gd+1. It can also be verified that ({atop {E}}langle v| {W}_{i,k}rangle {langle {W}_{i,k}| urangle }_{E}=0) if ({vert vrangle }_{E}) or ({vert urangle }_{E}) are not both in Gk. In other words, if ({vert urangle }_{E}) and ({leftvert vrightrangle }_{E}) are contained in different sets, then E(langle v| {W}_{i,k}rangle {langle {W}_{i,k}| urangle }_{E}=0). We can therefore move the sum over j in Eq. (26) outside the entropy S:
Since ({P}_{l}vert {C}_{j}rangle =0) if l ≠ d + 1 and ({P}_{l}vert {W}_{i,k}rangle =0) if l ≠ k, out of all the terms in the sum over j in Eq. (27) we are left with the terms ({P}_{d+1}vert {C}_{i}rangle =vert {C}_{i}rangle) and ({P}_{k}vert {W}_{k,i}rangle =vert {W}_{k,i}rangle), which greatly simplifies the expression for the Holevo bound:
We define d−1 vectors (vert {W}_{i}^{{prime} }rangle ={vert {v}_{0},ldots ,{v}_{0},{v}_{mu }^{(i)},{v}_{0},ldots ,{v}_{0}rangle }_{E},iin 1ldots d-1) such that (vert {W}_{i}^{{prime} }rangle otimes vert {p}_{0}rangle =vert {W}_{i,d}rangle) and (vert {W}_{i,j}rangle) are equivalent up to reordering the order of the time-bins. Since the entropy is additive for independent systems, rearranging the order of the terms in Eq. (28), we get:
Repeating the above steps from the Holevo bound on the channel between Alice and Eve yields:
To show that the Holevo of the channel between Eve and Bob is higher than the Holveo of Eve and Alics, we notice that ({chi }_{BE}-{chi }_{AE}=mathop{sum }nolimits_{i = 1}^{d-1}Sleft(Qvert {W}_{i}^{{prime} }rangle langle {W}_{i}^{{prime} }vert right)-Sleft(mathop{sum }nolimits_{i = 1}^{d-1}Qvert {W}_{i}^{{prime} }rangle langle {W}_{i}^{{prime} }vert right)=(d-1)S(Q)-Sleft(mathop{sum }nolimits_{i = 1}^{d-1}Qvert {W}_{i}^{{prime} }rangle langle {W}_{i}^{{prime} }vert right)). The dimension of the matrix in the second term is at most d−1 and thus it cannot have more than d−1 nonzero eigenvalues. The maximal entropy of the second term is achieved when all the eigenvalues are equal, and since its trace is (d−1)Q, we conclude that (mathop{sum }nolimits_{i = 1}^{d-1}Qvert {W}_{i}^{{prime} }rangle langle {W}_{i}^{{prime} }vert le (d-1)S(Q)). This can also be seen intuitively, as Eve’s information over Alice or Bob’s state is the same when the correct qudit was transferred, but when an error was passed Eve knows for sure what Bob got but has only partial certainty over what Alice sent. This yields that the Holevo-information will be maximal with Bob.
To calculate the entropy of the above matrices, we need to find their eigenvalues. We notice that both (vert {W}_{i}^{{prime} }rangle) and (vert {C}_{i}rangle) have the same form, (vert u,ldots u,v,u,ldots ,urangle) for some dimension (d or d−1). We now find, in general, the eigenvalues of a matrix (M={sum }_{i = 1ldots n}{{nterms}atop{overbrace{vert u,ldots u,{v}^{(i)},u,ldots ,urangle }}}langle u,ldots u,{v}^{(i)},u,ldots ,uvert). We can view (vert vrangle) as (vert vrangle =alpha vert urangle +beta vert {u}^{perp }rangle ,s.t.,langle u| {u}^{perp }rangle =0) and (vert {u}^{perp }rangle) is a unit vector, which gives us ∣〈v∣v〉∣2 = ∣α∣2 + ∣β∣2 = 1 and α = 〈u∣v〉. Now we can define the vectors (vert Urangle =vert u,ldots urangle) and (vert {V}_{i}rangle =vert u,ldots u,{u}^{perp (i)},u,ldots ,urangle) all orthogonal to each other, and get from linearity (M={sum }_{i = 1ldots n}(alpha vert Urangle +beta vert {V}_{i}rangle )({alpha }^{* }langle Uvert +{beta }^{* }langle {V}_{i}vert )=n| alpha {| }^{2}vert Urangle langle Uvert +{sum }_{i = 1ldots n}left(alpha {beta }^{* }vert Urangle langle {V}_{i}vert +{alpha }^{* }beta vert {V}_{i}rangle langle Uvert +| beta {| }^{2}vert {V}_{i}rangle langle {V}_{i}vert right)). By narrowing the matrix to the space spanned by (vert Urangle) and (vert {V}_{i}rangle), we obtain the following:
To obtain the eigenvalues M we can find the roots of the characteristic polynomial of ({M}^{{prime} }) and add ∣β∣2 to all of them. (| lambda I-{M}^{{prime} }| =(lambda -n| alpha {| }^{2}+| beta {| }^{2}){lambda }^{n}-n| alpha {| }^{2}| beta {| }^{2}{lambda }^{n-1}={lambda }^{n-1}(lambda +| beta {| }^{2})(lambda -n| alpha {| }^{2})), so the eigenvalues of ({M}^{{prime} }) are n∣α∣2, − ∣β∣2, and 0 with multiplicity n−1. Therefore, the eigenvalues of M are n∣α∣2 + ∣β∣2, 0, and ∣β∣2 with multiplicity n−1, where the zero eigenvalue does not affect the entropy.
Substituting the above eigenvalues into the expression for Holevo bound on Bob–Eve channel Eq. (29) information yields:
Imposing the unitary constraint for 〈v0∣vμ〉 = e−μ/2, and noticing that the first line in Eq. (32) can be simplified by (S(frac{1}{d}A)-frac{1}{d}S(A)=sum -frac{{lambda }_{i}}{d}{log }_{2}(frac{{lambda }_{i}}{d})-frac{1}{d}sum -{lambda }_{i}{log }_{2}({lambda }_{i})=S(frac{1}{d})sum {lambda }_{i}), yields the following expression for the Holevo bound:
To maximize χBE it is enough to minimize 〈v0∣pμ〉 under the constraints of Eqs. (21) and (22). The optimization can be done analytically using a parametric representation of (vert {v}_{0}rangle,vert {p}_{u}rangle ,vert {v}_{u}rangle) in 3-D space53. This yields:
Equations (33) and (34) provide the maximal entropy Eve can extract from the system as a function of the QBER Q, the visibility V, the occupation μ and dimension size d.
Detailed photon detection rate analysis
One of the features of our d-dimensional qudits is that it extends each qudit over d time-bins. In practice, the expectation time per received qudit is limited by the dead time of the detector. In the detector’s saturation regime, the dead time of the detector is similar to the time between successive detection events. Therefore, in this regime, the detector behavior depends on the previous detections. For simplicity, we assume independent and identically distributed behavior, i.e. each click has the same probability distribution as the others, and all are mutually independent.
To calculate the received bit rate as a function of the dead time of the detectors, we write the expectation value for the number of detection events in the time window Δt as clicks(Δt) = rΔt, where r is the detection rate. Assuming detection events are uncorrelated, we can express clicks(Δt) by clicks(t) = P(click)(1 + clicks(Δt−T−τ)) + (1−P(click))clicks(Δt−τ), where T is the detector dead time, τ is the pulse duration and P(click) is the probability a qudit will be recorded by the detector. For detector efficiency ξ, dimension d and occupation (mu ,P(click)=frac{xi mu }{d}). We, therefore, get that
from which we can extract the received detection rate r:
The lower bound for the secure key rate generation per second is given by the secure rate per detected photon (Eq. (14)), which is the outcome of the optimization problem, divided by the detection rate
where pdet is the probability that Bob detects a single photon in the packet, and d+1 time-bins are required to encode a qudit and separate the packets from each other.
The saturation regime refers to the case where the detection rate saturates, namely when ({T},gg ,tau ,frac{d}{xi mu }). Most of the deployed systems operate in this regime35, in order to extract higher key rates. In this regime, the raw detection rate is limited by the dead time of Bob’s detector, and not by the pulse occupation or the rate at which Alice sends her photons. Thus, even though d-dimensional encoding reduces the rate of photons sent by Alice, it does not lower the detection rate, while it enhances the number of bits received by Bob logarithmically with d. In principle, the eavesdropper may obtain more information from the d-dimensional encoding. However, our analysis shows that in the saturated regime, the secure key rate also increases.
Detailed secure key rate lower bound analysis
Secure key rate formula derivation
To directly derive Eq. (14) we follow the derivation of the secure key rate lower bound outlined by Berta et al.66. To derive the secure key rate bound, Berta et al. rely on the secure key rate bound obtained by Devateck and Winter58, and the entropic uncertainty relation. We assume that the eavesdropper creates a quantum state ρABE, and distributes the A and B parts to the two users, Alice and Bob. To generate the key, Alice and Bob measure the states they receive, with Alice’s possible measurements denoted by RA and SA and Bob’s by RB and SB.
Then by ref. 66, the secure key rate R is lower bounded by (Rge lo{g}_{2}frac{1}{c}-H({R}_{A}| {R}_{B})-H({S}_{A}| {S}_{B})), where c = maxj,k∣〈ψj∣ϕk〉∣2. Here (vert {psi }_{j}rangle) and (vert {phi }_{k}rangle) are the eigenvectors of RA and SA, respectively. For d dimensional states, the term (lo{g}_{2}frac{1}{c}) cannot exceed log2d, and equality is achieved when the eigenvectors of RA and SA represent two mutually unbiased bases, as in our case. The terms H(SA∣SB) and H(RA∣RB) correspond to the number of extra bits that are needed to reconstruct the value of SA using SB and RA using RB, respectively.
If the measurement outcomes of Alice and Bob in the base S(R) agree with probabilities of 1−ϵ (1−δ), then H(SA∣SB) and H(RA∣RB) are maximized for the following uniform probability distributions:
Therefore, H(SA∣SB) and H(RA∣RB) are bounded by hd(ϵ) and hd(δ), where ({h}_{d}(x)=-xlog frac{x}{d-1}-(1-x)log (1-x)) is the Shanon entropy of the distribution. Restricted to the case where d = 2, this reproduces the lower bound that appears in Morder et al.38.
Squashing model
The information known by Alice and Bob about the state can be represented by known expectation values of measurements. In order to numerically obtain the secure key rate lower bound it is necessary to formulate the measurement description in a finite dimensional form. While Alice’s subsystem has a finite dimension, Bob’s subsystem is defined by coherent states that are represented by an infinite number of Fock states. One can employ the squash model argument where measurements are decomposed into applying a map that transforms the incoming signal to a finite-dimensional output state in which low-dimensional measurements are performed64,65.
Here we extend the squashing model presented by Morder et al.37. The squshing model maps Bob’s states that contain more than one photon to an auxiliary state (leftvert auxrightrangle)64,65. Note that for this, one needs to assume that Bob can actively route the photons to the data line or the monitoring line. This squashing map is physical because we explicitly describe it in terms of measurements and conditional signal state preparations. Since this map can even be given to Eve, its output state lowers the key generation capabilities of Alice and Bob.
Bob’s space in the squashing model consists of 2+d states: (leftvert {rm{vac}}rightrangle) represents no photons in the packet, (leftvert trightrangle) corresponds to a single photon at time t and no photons elsewhere, and (leftvert auxrightrangle) denotes two or more photons in the packet.
The shared state
In this protocol, Alice sends an occupied pulse at each time-bin with a probability of 1/d and an empty time-bin otherwise. For a packet defined as m frames of d successive pulses, Alice’s state is encoded in a 2d vector space, where a two-dimensional representation indicates whether an occupied pulse was sent or not at each time-bin t ∈ 1, …, m ⋅ d. Therefore, the shared state, before considering losses and errors in the channel, is given by ({rho }_{AB}={leftvert psi rightrangle }_{AB}{leftlangle psi rightvert }_{AB}), where
Here, N = i1 + … + id represents the number of occupied pulses in the packet, and (tilde{t}in {{rm{vac}},1,ldots ,d,{rm{aux}}}) denotes Bob’s states corresponding to no detected photons, a single detected photon, and two or more detected photons in a packet. This model estimates accurately the key rate when μηm ≪ 1. Otherwise, this lower bound is correct, but far from being tight.
Channel loss
We modeled the losses in the channel using a beam splitter with transmittance η. Mathematically, the pure state after the beam splitter is described as:
where (sqrt{{mu }_{eta }}=sqrt{mu (1-eta )}) and (sqrt{{mu }_{r}}=sqrt{mu eta }). ({B}^{{prime} }) represents the unused port of the beam splitter that goes to an inaccessible environment. Since the environment is inaccessible, we trace it out, defining ({rho }_{loss}={{rm{Tr}}}_{{B}^{{prime} }}{leftvert psi rightrangle }_{AB{B}^{{prime} }}{leftlangle psi rightvert }_{AB{B}^{{prime} }}).
Error model
We model a bit flip error using temporal incoherent bit flip of the time-bins with a small probability of ed:
where:
Measurement description
The information known by Alice and Bob about the state ρAB can be represented by known expectation values of two types of projection operators, which correspond to data line measurements and coherence measurements.
For a data line measurement, where a single photon is detected in time-bin t = 1, 2, …, m ⋅ d, the corresponding measurement operator Mt is defined as:
Here, ϵ represents the dark count probability at Bob’s detectors, and (leftvert trightrangle) denotes a single photon state at time-bin t.
In addition to data line measurements, Bob performs coherence measurements on successive pulses using the monitoring line. We use the outcome label κ = (c, ±) to represent the coherence measurements, where c = 2, …, m ⋅ d denotes the time-bin of the last of the two interfering pulses, and ± represents the bright or dark detector. We assume a misalignment error with probability em that the outcome interference of two coherent pulses in the beamsplitter exits through the wrong output port. This error leads to a reduction in visibility in the monitoring line, which is independent of dimension. To consider both the misalignment error em and the dark count probability ϵ at the monitoring line, the detection of a signal at time t at the monitoring line is modeled by the operator:
Here, (vert {chi }_{c}^{pm }rangle =frac{1}{sqrt{2}}(vert crangle pm vert c-1rangle )) represents the superposition state formed by pulses at time-bins c and c − 1.
Eve’s constraints
Since Eve’s action can not change Alice’s state, the reduced density matrix ({rho }_{A}={{rm{tr}}}_{BE}({rho }_{ABE})) remains fixed and is determined by the source state. To incorporate this information, we can include the expectation values of Tk ⊗ I, where Tk represents a complete tomographic operator set on Alice’s system.
In particular, since each time-bin can be either occupied or empty, Alice’s state can be represented as a collection of d two-dimensional systems. Any qudit state ρA can be expressed as:
Here, ({hat{sigma }}_{i}) represents the Pauli matrices, and Si are the Stokes parameters for multiple qubits. These equations provide us with 4d−1 constraints that completely determine Alice’s state.
In addition, for any label in the monitoring line and in the data line, ν ∈ {c±, t}, and choosing a state i in Alice’s space, we obtain the following condition on the state ρopt:
where we define ({M}_{nu }^{perfect}) by substituting zero errors in Eqs. (42), (43) above, and ({M}_{nu }^{imperfect}) by substituting the errors according to Bob’s detectors presented above. ρAB is defined in Eq. (40).
Sifting maps, the bit error, and the phase error
The sifting process is obtained by announcements that are presented using maps Λ that operate on the quantum state. Bob’s announcement of registering a single photon event is presented as a map ({Lambda }^{B}(rho )={F}_{B,sigma ,k}rho {F}_{B,sigma ,k}^{dagger }) that maps the state to the logical space (bar{B}) depending on the permutation σ and the frame k. FB,σ,k is defined as:
Alice’s filter projects each state at Alice A space to Alice logical space (bar{A}) given the transformation FA,σ,k:
where NV is the number of permutations of the state V that yield a key, i.e. that induce at least one frame with only one occupied time-bin according to the permutation σ. We note that NV depends on the number of occupied time-bins in V.
The bit error ϵ, and the phase error δ are the probabilities that Alice and Bob do not agree on the bit value in the d-dimensional computational space and in the d-dimentinal discrete Furrier basis, respectively. Here we calculate the average errors (bar{delta },bar{epsilon }) over all possible announcements defined by Alice’s permutation σ and Bob’s detected frame index k. These quantities are used to calculate the secure key rate by Eq. 14.
To determine (bar{delta }) and (bar{epsilon }), both parties first apply the filter operator on the shard state, FA,σ,k, FB,σ,k defined above. Then, to determine (bar{epsilon }) both parties project the state onto the discrete d logical states ({vert {i}_{z}rangle }_{bar{A}}in bar{A}) and ({vert {i}_{z}rangle }_{bar{B}}in bar{B}). The spaces (bar{A},bar{B}) are d-dimensional logical spaces that are obtained by filter operations. Similarly, to determine (bar{delta },k) both parties project their state onto the discrete d-dimentinal discrete Fourier space obtained by applying DFT on the logical states: ({vert {i}_{x}rangle }_{bar{A}}=DFT{vert {i}_{z}rangle }_{bar{A}}) and ({vert {i}_{x}rangle }_{bar{B}}=DF{T}^{dagger }{vert {i}_{z}rangle }_{bar{B}}). Formerly, the average phase error (bar{epsilon }) and the average phase error (bar{delta }) are defined as:
and
where G is the gain, i.e. the probability of a conclusive announcement, and:
Numerical optimization
In our implementation of the semi-definite program, we employ the packages YALMIP92 and MOSEK93.

Responses