Secure healthcare data management using multimodal image fusion and dual watermarking

Introduction
The proliferation of digital healthcare systems has dramatically altered the landscape of medical data management, offering significant advantages such as enhanced diagnostics, improved data accessibility, and streamlined patient care1. However, this paradigm shift has also introduced vulnerabilities, making sensitive medical data susceptible to unauthorized access, tampering, and breaches2. Ensuring the confidentiality, integrity, and authenticity of healthcare data, particularly in the context of medical imaging, is paramount for safeguarding patient privacy and maintaining the trustworthiness of medical diagnoses3. This is especially critical in telehealth applications, where medical images and data are transmitted over networks, making them more vulnerable to cyber threats. Figure 1 highlights the primary security risks in healthcare data, including breaches, privacy threats, and access vulnerabilities.
Major security issues in healthcare data.
Comparative analysis of security mechanisms for healthcare data protection
Various security mechanisms, including steganography, cryptography, and watermarking, have been explored to address these concerns. While each of these techniques serves a unique function in securing data, an optimal security framework requires a hybrid approach that combines multiple techniques.
Table 1 presents a comparative analysis of these techniques, highlighting their capabilities, limitations, and relevance in secure healthcare data management.
As shown in Table 1, while steganography provides covert communication by hiding the presence of data, it lacks robustness. Cryptography ensures strong security by encrypting data but does not conceal its existence. Watermarking, on the other hand, embeds identifying data within medical images, ensuring authenticity and security. However, standalone watermarking techniques may not provide adequate protection against unauthorized modifications or extraction attempts.
Medical imaging modalities such as magnetic resonance imaging (MRI) and single photon emission computed tomography/positron emission tomography (SPECT/PET) generate substantial volumes of sensitive data. Protecting this data against cyber threats and data breaches is vital, especially as telehealth expands. Watermarking techniques have emerged as a promising solution to ensure data authenticity and confidentiality by embedding secure information directly into medical images4. Watermarking provides a robust mechanism for verifying data ownership, integrity, and authenticity, ensuring that healthcare data remains secure during transmission and storage.
Multimodal image fusion, particularly the combination of MRI and SPECT/PET images, has garnered significant attention in recent years. These imaging modalities provide complementary information, MRI offers detailed structural insights, while SPECT/PET contributes functional data. Fusion of these images enhances the overall diagnostic potential by producing a richer host image5. The fused image serves as an ideal candidate for embedding sensitive patient information, such as identification documents (e.g., Aadhaar card) of the patient.
Contribution
This work proposes a secure and efficient approach for protecting medical images through multimodal fusion, dual watermarking, and encryption. The key contributions are:
-
1.
Multimodal image fusion A Laplacian Redecomposition-based fusion technique integrates MRI and SPECT/PET images, preserving both anatomical and functional details, making the fused image an effective host for watermarking.
-
2.
Dual watermarking for identity and integrity Protection The proposed scheme embeds an Aadhaar card image for patient identity verification and a hash value of the cover image for integrity verification.
-
3.
Optimized integration of transforms The embedding scheme integrates Lifting Wavelet Transform (LWT), Hessenberg Decomposition (HD), and Singular Value Decomposition (SVD)to enhance robustness against attacks.
-
4.
Spatial domain hash concealment The Pseudo Magic Cube technique6 embeds the hash value imperceptibly, ensuring effective tamper detection.
-
5.
Encryption for secure transmission A Latin Square-based PSDCLS7 encryption scheme ensures confidentiality during transmission and storage.
-
6.
Performance evaluation Extensive experiments demonstrate high imperceptibility and robustness, achieving PSNR (37.7895 dB), SSIM (0.9993), and NC (0.9998).
Novelty
The novelty of this research lies in its integrated approach of multimodal image fusion, dual watermarking, and encryption. The key novel aspects are:
-
1.
Laplacian redecomposition-based fusion Unlike traditional methods, this technique8 segments redundant and complementary information separately, preserving finer details for diagnostic applications.
-
2.
Simultaneous identity and integrity protection Instead of embedding only metadata, the proposed scheme simultaneously embeds Aadhaar card details of the patient and a hash value, ensuring both authentication and tamper detection.
-
3.
Combination of spatial and transform domains The hybrid approach integrates LWT9, HD10, and SVD11 in the transform domain to enhance robustness against various attacks, while the Pseudo Magic Cube technique improves embedding capacity in the spatial domain.
-
4.
Improved security through dual watermarking and encryption The proposed approach embeds two watermarks within the cover media, simultaneously ensuring both copy protection and content security. Additionally, integrating encryption scheme enhances the overall security of the framework.
This framework provides a secure and practical solution for safeguarding sensitive medical data in digital healthcare environments, ensuring authenticity, confidentiality, and resilience against attacks. The subsequent sections present a detailed review of related work, the proposed methodology, and comprehensive experimental evaluations.
The remainder of this paper is structured as follows: section “Related works” provides an in-depth overview of the relevant literature. Section “Proposed methodology” delves into the details of the proposed framework. Section “Result analysis” thoroughly evaluates the performance of the framework. Lastly, section “Conclusion” presents a concise summary of the paper.
Related works
Recent watermarking techniques focus on securing healthcare data in telehealth applications, ensuring integrity, privacy, and copyright protection. This section reviews key approaches enhancing data security and authenticity.
Anand et al.12 introduced MIWET, a robust watermarking scheme for protecting medical data. MIWET leverages NSST and DTCWT for multimodal image fusion to generate a watermark, which is then embedded into a carrier image using NSST, BEMD, and MSVD. HOG-based optimization ensures a balance between visual quality and robustness. The marked image is encrypted for added security, achieving impressive imperceptibility and robustness. However, further optimization is needed to reduce computational complexity and enhance encryption resilience against sophisticated attacks. Singh et al.13 proposed a secure watermarking scheme, WatMIF, for telehealth applications, leveraging multimodal image fusion and encryption. The algorithm consists of three core steps: encrypting the host media using a key-based method, fusing MRI and CT images with NSCT to create a watermark, and embedding this fused mark into the encrypted host media using RDWT and RSVD. HOG-based optimization balances visual quality and robustness, and a denoising CNN (DnCNN) further enhances robustness at the receiver side. While WatMIF demonstrates high imperceptibility and robustness, there remains potential to reduce computational complexity and enhance encryption against sophisticated attacks. Vaidya14 proposed a medical image watermarking technique using LWT-DWT domain, enhanced with Arnold Cat map for added security, demonstrating high imperceptibility, robustness against various image processing attacks, and significant improvements in medical image privacy. However, the encryption method’s security level may not be optimal, suggesting room for further enhancement. Singh et al.15 proposed a robust e-healthcare watermarking algorithm by fusing MRI and PET images using NSST. The fused image is embedded into a cover image through IWT, QR decomposition, and SVD, ensuring both imperceptibility and robustness. A 3D chaotic map is employed for encrypting the marked image. The results demonstrate strong resistance to attacks, high visual quality, and enhanced robustness compared to existing methods, although the approach is currently limited to grayscale images. Meng et al.16 propose a hybrid data hiding scheme for medical images that combines Advanced Encryption Standard-Galois/Counter Mode (AES-GCM) encryption and Fused Transform-Based Method (FTBM) watermarking. Patient information is first encrypted using AES-GCM, then embedded into the Region of Non-interest (RONI) of the medical image using FTBM. Intensity-based image segmentation is used to identify the RONI. The FTBM integrates HD, SVD, and Discrete Wavelet Transform (DWT) for robust and imperceptible watermark embedding. Experimental results indicate that the proposed technique outperforms existing methods in terms of imperceptibility, robustness, and security. The method is also efficient in terms of embedding and extraction times. However, the intensity-based image segmentation may not be effective for images with complex structures or textures where the ROI and RONI have similar intensity values.
Bhardwaj17 proposed a dual-image reversible data hiding scheme for secure e-healthcare data transfer. Their approach involves encrypting both the cover image and secret data using Paillier cryptography, followed by embedding the encrypted data into the encrypted cover image. A fragile watermark is also embedded to authenticate content on the recipient side. While the scheme offers high embedding capacity and robustness, its embedding process is computationally intensive, which might be a limitation in real-time applications. Awasthi et al.18 proposed a novel watermarking scheme to secure the integrity of medical images for telehealth applications using ANFIS optimization and blockchain authentication. The scheme combines redundant discrete wavelet transform (RDWT) and multiresolution singular value decomposition (MSVD) to embed a hybrid watermark, consisting of Aadhar and barcode images, into the cover image. ANFIS is used to determine the optimal embedding strength, ensuring a balance between robustness and imperceptibility. Blockchain encryption further enhances security by authenticating the watermark. Experimental results demonstrate that the scheme is highly robust and imperceptible; however, its computational complexity may impact real-time performance, and further testing against diverse attack scenarios is needed. Khaldi et al.19 presented a watermarking scheme for secure medical image transmission in telemedicine, utilizing RDWT and Schur decomposition. The watermark, comprising an encrypted patient photo and information fingerprint, is embedded in the mid-frequency coefficients to balance imperceptibility and robustness. Experimental results show strong resistance to attacks like JPEG compression and noise addition while preserving image integrity. However, minor deviations from the ideal normalized correlation of 1 indicate potential for further improvement. Priyanka et al.20 propose a region-based hybrid medical image watermarking scheme for secure transmission in the Internet of Medical Things (IoMT). The method distinguishes between the Region of Interest (ROI), which contains critical diagnostic information and requires high integrity, and the Region of Non-Interest (RONI), where the watermark is embedded. Adaptive LSB substitution is used to embed tamper detection and recovery bits in the ROI, ensuring high imperceptibility and accuracy. The RONI is watermarked using DWT-SVD to embed a QR code, encrypted EPR data, and recovery bits, ensuring robustness. Experimental results demonstrate high imperceptibility, robustness, and effective tamper detection and recovery. However, limitations include vulnerability to salt and pepper noise attacks. Taj et al.21 propose a SURF and SVD-based zero-watermarking scheme to enhance medical image integrity. The method uses SURF for precise feature extraction and SVD for embedding a watermark in the frequency domain without altering image quality. The embedded watermark is imperceptible, maintaining diagnostic details while showing strong robustness against attacks like Gaussian noise, JPEG compression, and geometric distortions. However, limitations include potential performance drops in extremely aggressive attacks, such as extensive cropping, and the computational complexity associated with feature extraction and frequency domain embedding, which may impact real-time applications.
Soualmi et al.22 proposed a hybrid watermarking approach integrating Imperialistic Competitive Algorithm (ICA), Speeded-Up Robust Features (SURF), and Discrete Cosine Transform (DCT) to optimize watermark embedding locations, improving resilience against geometric and signal processing attacks. Similarly, Soualmi et al.23 introduced a chaotic sequence-based blind watermarking scheme that incorporates the A-star algorithm and DCT to enhance imperceptibility, robustness, and processing efficiency, demonstrating high resistance to filtering, rotation, and JPEG compression.
Fikri et al.24 developed an IWT-SVD based dual watermarking method, leveraging human visual characteristics to optimize embedding while ensuring robustness against noise and compression. Ng et al.25 proposed an IWT and SVD-based scheme incorporating authentication bits in the Least Significant Bit (LSB) to enhance tamper detection and image integrity verification.
Ridwan et al.26 introduced a Schur decomposition-based watermarking method employing dual embedding, achieving high peak signal-to-noise ratio (PSNR) and normalized correlation (NC) values under multiple attacks. Gen at al.27 presented a dual watermarking scheme based on Discrete Wavelet Transform (DWT) for image integrity verification and copyright protection. It embeds a robust watermark in the frequency domain for ownership verification and a fragile watermark in the spatial domain for tamper detection.
Proposed methodology
Our proposed methodology comprises three primary stages. First, we generate a fused image from MRI and SPECT/PET images to serve as the host image in the embedding process. Second, we embed the patient’s Aadhaar card image watermark into the host image to create a watermarked image. Subsequently, we embed the hash value (64 characters using SHA-256) of the host image within the watermarked image using a pseudo-magic cube algorithm to generate the final watermarked image. Finally, we apply encryption to the final watermarked image for enhancing security. In the third stage, we extract the hash value and Aadhaar image watermark from the final watermarked image, effectively recovering the embedded watermarks.
Fusion of multimodal medical images to generate a host image
The Laplacian Redecomposition-Based Medical Image Fusion Algorithm begins with two source images, (A) (anatomical) and (B) (functional), and produces a fused image, (F). Initially, Gradient Domain Image Enhancement (GDIE) is applied to enhance details and reduce noise in the source images. This involves calculating the Maximum Local Difference (MLD) for each pixel using a (3times 3) window to capture local gradients:
where (Z(x)) is the sum of pixel values in predefined directions. A threshold (T), derived from the sorted (D(i, j)), segments the image into edge, detail, and background intervals. The Adaptive High-Frequency Information Lifting Coefficient, (C(i,j)), adjusts the enhancement intensity based on (D(i,j)) and an interval-fitting function (Y_1(x)):
Local gradient information is computed using:
and remapped via:
where (Y_2(x)) is a remapping function. Convolution of (g_2) with the source image yields the enhanced images:
Next, Laplacian Pyramid (LP) Decomposition is performed on the enhanced images, resulting in high-frequency sub-band images (HSI), (L_{gamma mu }(i,j)), and low-frequency sub-band images (LSI), (G_{tau mu }(i,j)), as:
The decision graph redecomposition (DGR) algorithm is applied to the HSI to separate redundant from complementary information. Global decision graphs are created for pixel value analysis, and classifiers locate redundant and complementary information. Overlapping domain images, (O_{gamma mu }(i,j)), containing redundant information, are computed as:
while non-overlapping domain images, (N_{gamma mu }(i,j)), containing complementary information, are calculated as:
Fusion rules are then employed to combine these components. For the LSIs, the local energy maximum (LEM) fusion rule is used to compute a fused LSI. The LEM value, (Q_mu (i,j)), is:
where (lambda) is a filter template. The fused LSI is determined as:
Overlapping domain images are fused using the OD fusion rule, calculated via Local Decision Maximums (LDM):
Non-overlapping domain images are fused using a simple addition operation:
To finalize the fusion process, the Inverse Redecomposition Scheme (IRS) combines high-frequency images from the OD and NOD fusions into a single high-frequency sub-band image while minimizing artifacts. The fused high-frequency image is obtained as:
Finally, the fused image, (F(i,j)), is reconstructed by combining the fused LSI and high-frequency sub-band image using an inverse LP transform:
This algorithm effectively preserves structural and functional information in fused medical images, minimizing color distortion and artifacts, although the GDIE process can be computationally intensive. The fusion of MRI and SPECT image is illustrated in Fig. 2. Various notations used in Algorithm 1 are shown in Table 2.

LRD-based Medical Image Fusion
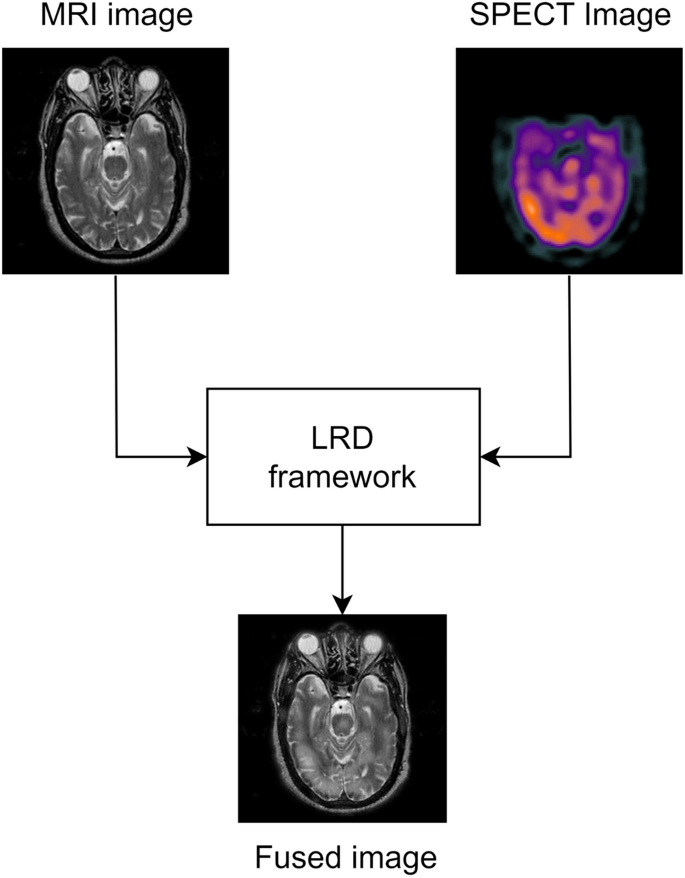
Multimodal medical image fusion.
Watermark embedding and extraction process
Algorithm 2 outlines the embedding procedure with encryption that integrates watermarking and cryptographic technique to secure a cover image, ultimately producing an encrypted watermarked image. The process begins by accepting three inputs: the cover image (C), a scaling factor (alpha), and the watermark image (W). The cover image (C) is decomposed into four sub-bands-(LL, LH, HL,) and (HH)-using the Lifting wavelet transform (LWT). The low-frequency sub-band (LL) is then subjected to a Hessenberg decomposition (HD), resulting in matrices (P) and (H).
Subsequently, singular value decomposition (SVD) is applied to both the matrix (H) from the cover image and the watermark image (W), yielding singular values (S_H) and (S_W) along with their corresponding matrices (U_H, V_H) and (U_W, V_W). The watermark embedding is performed by adding (S_H) to the scaled singular values of the watermark (alpha times S_W), producing a new set of singular values (S_{HW}). The watermarked matrix (H_W) is then reconstructed by multiplying (U_H), (S_{HW}), and the transpose of (V_H).
The modified low-frequency sub-band (LL_{new}) is obtained by transforming (H_W) back using the matrix (P). An inverse LWT (ILWT) is then applied to (LL_{new}) along with the other sub-bands (LH, HL,) and (HH) to reconstruct the image (C’), effectively embedding the watermark into the cover image. A hash value is generated from the original cover image (C) and converted into a decimal sequence (dec_{wat}), which serves as the data for further embedding.
To enhance security, a magic cube (MC) of a specified size (N) and a random sequence (Rand_{seq}) are generated using a seed (R_{seed}). For each decimal value in (dec_{wat}), three pixels in the watermarked image (C’) are selected based on (Rand_{seq}) and modified using the ‘EmbeddingMCF‘ function. This function embeds each decimal value into three separate pixels, updating the pixel values in (Final_{img}).
Finally, the image (Final_{img}) undergoes an encryption process to produce (Enc_{img}), the encrypted, watermarked image. This image is then returned as the output of the algorithm. Overall, the procedure seamlessly combines watermarking and encryption techniques, utilizing a pseudo magic cube to enhance the security and integrity of cover image.
The block diagram of the proposed methodology is shown in the Fig. 3. The watermark extraction process, outlined in Algorithm 3, is performed by reversing the steps of the embedding procedure and retrieve’s the Aadhaar card and hash value.
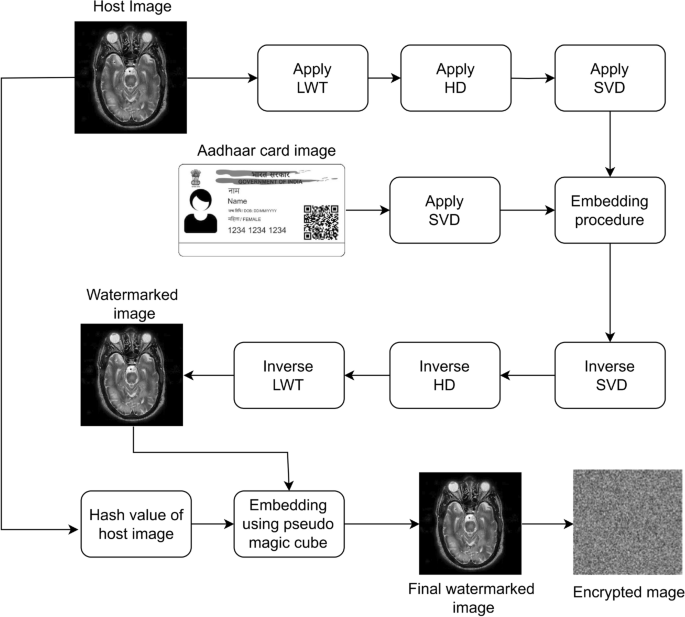
Block diagram of the proposed algorithm.

Watermark Embedding
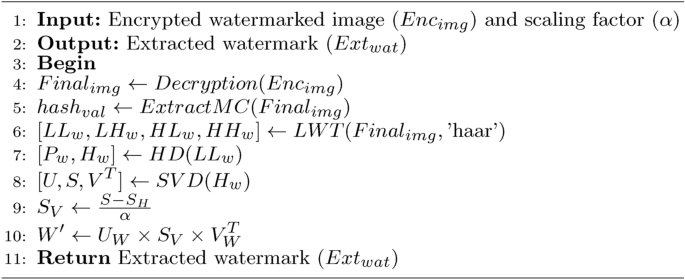
Watermark extraction
Encryption of watermarked image
The PSDCLS encryption algorithm7 for a fused multimodal medical image derived from MRI and SPECT/PET begins by generating a hash-based key using the SHA-256 hash of both the fused image and a user-defined secret key, which are concatenated to form a combined hash. Initial parameters (x_0) and (y_0) for a 2D Hénon-Sine chaotic map are derived from this hash, along with control parameters (a) and (b). The chaotic map generates random sequences to construct a Latin square, which is then used for simultaneous diffusion and confusion. A diffusion key matrix is created by taking the modulo 256 of the Latin square. The encryption process applies vertical diffusion-confusion by XORing the fused image pixels with the diffusion key matrix as guided by the Latin square. This is followed by horizontal diffusion-confusion, where pixel values are added and modulated with the diffusion key. The resulting matrix, after both vertical and horizontal transformations, is the final encrypted fused medical image, ensuring secure and efficient scrambling of pixel values. The decryption process involves reversing the encryption operations to retrieve the original image. Algorithm 4 shows the encryption procedure.

Encryption Phase of PSDCLS
Evaluation metrics
In evaluating the effectiveness of the watermarking process, four primary metrics are utilized: Structural Similarity Index (SSIM), Correlation Coefficient (NC), Peak Signal-to-Noise Ratio (PSNR), and the measures of NPCR and UACI.
Structural similarity index (SSIM)
SSIM12 assesses the similarity between the cover and watermarked images, reflecting human visual perception. It evaluates the imperceptibility of the watermark, ensuring that the watermark embedding process does not noticeably alter the original image. SSIM values range from − 1 to (+) 1, with an ideal value of (+) 1 indicating perfect similarity. The formula for SSIM combines three factors: luminance, contrast, and structure, with each component calculated as follows:
Correlation coefficient (NC)
NC12 measures the similarity between the original and extracted watermarks, reflecting the robustness of the watermarking method. A higher NC value, ranging from 0 to 1, indicates stronger similarity, with an ideal NC of 1 showing perfect correlation. The formula for NC is given by:
Peak signal-to-noise ratio (PSNR)
PSNR12 is used to measure the quality of the watermarked image in comparison to the original. It reflects the degree of imperceptibility, with higher values indicating less noticeable differences. PSNR is ideally above 28 dB for acceptable quality. Its calculation involves Mean Squared Error (MSE) as follows:
NPCR and UACI
NPCR (number of pixels change rate) and UACI (unified average changing intensity)12 assess the security of the encryption process. NPCR measures the percentage of pixels that differ between two images, ideally reaching (+) 1 for complete change. UACI quantifies the average intensity change, with an ideal value of approximately 0.34 for a (512times 512) image. The NPCR and UACI values are calculated as:
Each of these metrics plays a vital role in analyzing the watermarking system’s overall performance, offering insights into both imperceptibility and robustness against potential attacks.
Result analysis
Experiments were conducted on a PC equipped with a 64-bit Windows 10, 2.40 GHz processor, 16 GB of RAM, and MATLAB R2020b for simulation. The MRI, PET, and SPECT test images were taken from the medical library of Harvard University, Cambridge, MA, USA28. Authenticity is ensured by embedding a grayscale Aadhaar card image watermark, sized (256times 256), within fused host images that are sized (512times 512), along with the 64-character hash value of the host image. An embedding factor, (alpha), of 0.05 was chosen to maintain a balance between imperceptibility and robustness. The results presented in the table highlight the performance of embedding a (256 times 256) Aadhaar card image watermark and hash value into fused medical images (MRI (+) SPECT or MRI (+) PET).

Experimental images.
The host image and watermarked image are shown in Fig. 4 and representative Aadhar card of patient is shown in the Fig. 3.
The proposed multimodal image fusion and watermarking framework demonstrates effective security and robustness in embedding sensitive medical data within fused images. Results from Tables 3 and 6 highlight the approach’s strong performance, where MRI and SPECT/PET fused images serve as host images for embedding a (256times 256) Aadhaar card watermark along with a hash value, achieving high visual fidelity and resilience against various attacks. PSNR values ranging from 36.4852 to 37.7895 dB signify minimal distortion in watermarked images, ensuring that image clarity is maintained, a critical requirement in medical imaging applications. Additionally, high SSIM values, consistently close to 1, reflect excellent preservation of structural integrity in cover images, which is essential for retaining diagnostic accuracy. Table 4 shows the performance analysis of our method at a different gain values. The highest PSNR of the proposed grayscale watermarking method is lower than the color image watermarking techniques presented by Ng et al.25 and Gen at al.27, PSNR of both method’s > 40 dB.
Table 5 evaluates the visual quality of the watermarked image at different gain factors subjectively, showing that lower values (e.g., 0.001) ensure excellent imperceptibility, while higher values (e.g., 0.5) noticeably degrade quality.
The watermark’s robustness is further demonstrated by NC values near 1 across all tested cases, indicating that the embedded Aadhaar card watermark can be accurately retrieved without degradation. This ensures the integrity of embedded data during transmission and storage. NPCR values, ranging from 0.9955 to 0.9964, underscore the method’s robustness against differential attacks, where substantial pixel value changes reinforce security by resisting attempts to detect patterns. UACI values, between 0.3299 and 0.3452, reveal balanced intensity variations across pixels, offering a judicious balance between security and imperceptibility, both of which are critical for safeguarding confidential medical data without affecting image quality.
The robustness of the proposed watermarking method is evaluated by comparing NC values with existing techniques under various attacks, as shown in Table 6. For Salt & Pepper noise, the proposed method achieves an NC value of 0.9716, which is slightly lower than22 and29, indicating reasonable resilience but some vulnerability to impulse noise. Against Gaussian noise, the proposed method performs well with an NC value of 0.9826, closely matching30 and significantly surpassing22, demonstrating strong robustness. For JPEG compression (quality factor 50), the proposed approach achieves the highest NC value of 0.9918, outperforming22,29, and31, highlighting superior resistance to lossy compression. Under median filtering ([2 2]), the proposed method attains an NC value of 0.9750, significantly improving upon29 (0.7549), showing effectiveness against nonlinear filtering. Additionally, for average filtering ([2 2] window size), the proposed approach achieves 0.9919, with no prior works providing comparative values. Overall, the proposed method demonstrates strong robustness, particularly against Gaussian noise, JPEG compression, and filtering attacks, outperforming existing techniques in several cases. While the performance under Salt & Pepper noise could be further optimized, the method remains highly effective for practical watermarking applications in digital image security.
Performance comparisons between MRI (+) SPECT and MRI (+) PET fused images reveal marginally higher PSNR values in MRI (+) PET cases, indicating a slight advantage in image quality preservation. This subtle variation illustrates the framework’s flexibility in handling different fusion types without compromising the embedded watermark’s security. Collectively, the consistently high PSNR, SSIM, and NC values across various attacks confirm the efficacy of the proposed approach in securing Aadhaar card information and a hash value within fused medical images, supporting a robust and secure watermarking method that upholds the integrity of critical diagnostic information while protecting patient privacy.
SIFT is employed to assess how well the watermarking method performs by analyzing and comparing the feature descriptors from both the original and watermarked images. The algorithm detects unique elements like edges, corners, and blobs within the images and represents them through local descriptors. The findings, as illustrated in Fig. 5, demonstrate a substantial number of matching features and very little distortion.
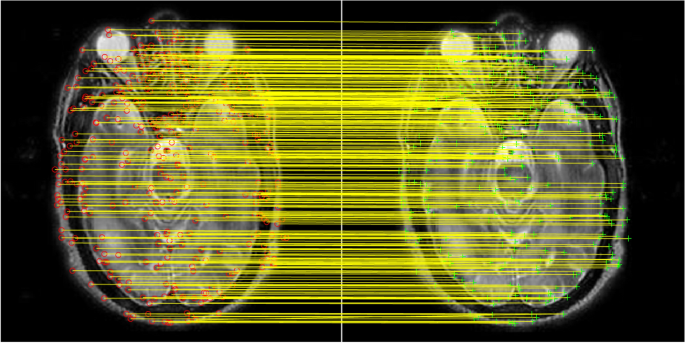
Subjective analysis using SIFT feature.
Security analysis
The histogram of an image represents the distribution of pixel intensity values. To ensure confidentiality, an image encryption algorithm should strive for a uniform histogram distribution, thereby eliminating any statistical correlations between the plaintext and ciphertext images. Figure 6 demonstrates the efficacy of our encryption scheme, where the histogram of the plaintext image exhibits a non-uniform distribution, whereas the ciphertext image’s histogram approximates a uniform distribution. Moreover, the histograms of encrypted images exhibit distinct characteristics, diverging significantly from their corresponding plaintext images. The key sensitivity analysis of the proposed scheme demonstrates an extremely high security level, with a key space of (2^{512}), making it resistant to brute-force attacks.
This uniformity in the histogram distribution of encrypted images prevents potential attackers from launching histogram-based attacks, which rely on statistical analysis to infer information about the plaintext image. Our encryption algorithm achieves this by effectively flattening the intensity distribution, rendering histogram analysis ineffective for inferring meaningful information about the original image. The encryption and decryption time for the host image ((512 times 512)) as shown in Fig. 6 is 0.041320 s and 0.039522 s respectively.
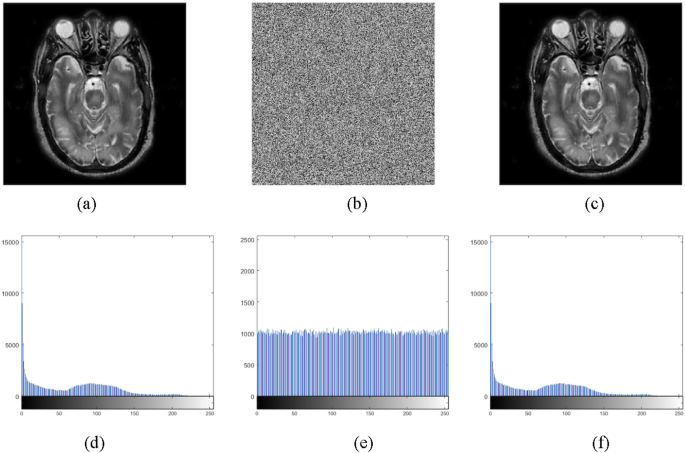
(a) Plain image, (b) corresponding cipher image, (c) decrypted image, (d) histogram of Plain image, (e) histogram of cipher image, (f) histogram of decrypted image.
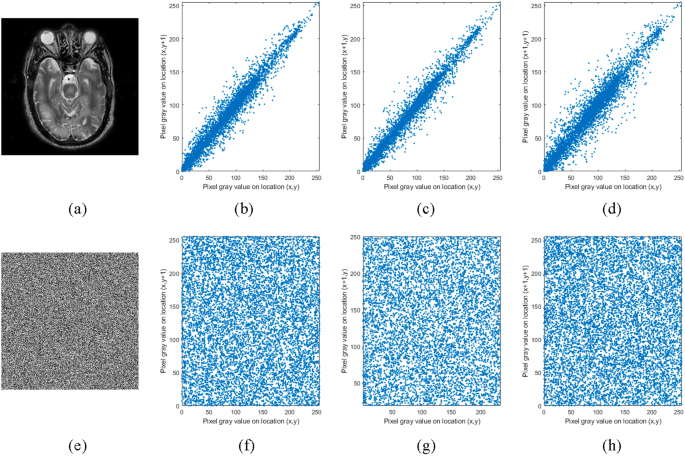
(a) Plain image, correlation of plain image in vertical, horizontal and diagonal direction is shown by (b), (c), (d) respectively. (e) Corresponding Cipher image, correlation of Cipher image in vertical, horizontal and diagonal direction is shown by (f), (g), (h) respectively.
Correlation Analysis in (h), (v), and (d) Directions: To assess the encryption’s effectiveness, correlation analysis is conducted across three axes: horizontal, vertical, and diagonal. The significantly low correlation values obtained for the encrypted image signify disrupted spatial relationships, increased randomness, and enhanced security. This analysis reaffirms the reliability of the encryption method in safeguarding image contents against unauthorized access. Figure 7 illustrates the pixel distributions of the plain and encrypted images across each directional axis.
The proposed method was evaluated against existing state-of-the-art approaches, as presented in Table 7, and demonstrated improved visual quality of the watermarked image. The proposed method achieves the highest PSNR (37.7895 dB), indicating minimal distortion, outperforming other method’s.
For SSIM, the proposed method attains 0.9993, ensuring superior structural preservation. While Chaudhary et al. (0.998) and Anand et al. (0.9950) perform well, Li et al. (0.9788) shows the most structural deviation. The results confirm that the proposed method achieves a better balance between imperceptibility and robustness.
The high PSNR and SSIM make the proposed technique more suitable for medical image security, ensuring minimal quality degradation while maintaining image integrity.
Table 8 presents a comparative analysis of the payload capacity of the proposed method against existing techniques. The results show that our method outperforms12,35,31 in terms of capacity.
The computational complexity of LWT-HD-SVD-based watermarking is primarily dominated by the HD and SVD step, which is (O(M^3)). The time complexity of LWT is O(N2). Thus, the overall time complexity can be approximated as:
where (N times N) is the size of the host image, (M times M) is the size of the LL sub-band and image watermark and (k) is the constant. This makes the scheme relatively efficient for practical applications.
Limitations and implications
Despite its strong security and robustness, the proposed framework has some limitations. The combination of Laplacian redecomposition-based fusion, LWT-HD-SVD watermarking, and PSDCLS encryption increases computational complexity, potentially limiting real-time medical applications. Additionally, its performance on high-resolution medical images remains untested. The framework also requires further evaluation against advanced cyber threats, such as adversarial attacks and side-channel exploits. Furthermore, its reliance on Aadhaar-based identity verification may pose privacy and regulatory concerns in regions with strict biometric data protection laws.
Future work can focus on optimizing real-time execution through hardware acceleration (FPGA/GPU) to enhance practical applicability. Evaluating performance on high-resolution medical images and integrating additional security mechanisms, such as blockchain-based authentication, could further improve robustness. Exploring non-biometric identity verification methods, like cryptographic signatures, may also address privacy concerns while ensuring data security.
Conclusion
This paper presents a comprehensive and robust framework for securing healthcare data using multimodal image fusion and watermarking techniques. By fusing MRI and SPECT/PET images and embedding patient identification details, such as Aadhaar card information and hash value, this method ensures the protection and integrity of critical medical data. The LWT, HD, SVD and pseudo magic cube contribute to the imperceptibility and robustness of the watermarking process, as evidenced by the consistently high PSNR, SSIM, and NC values. Additionally, the lossless encryption scheme adds an extra layer of security during the transmission of the watermarked images.
The results demonstrate that this approach not only preserves the structural integrity and diagnostic value of medical images but also ensures strong resilience against various image processing attacks. This framework offers a promising and practical solution for securing sensitive healthcare data in the evolving landscape of digital medical systems, addressing both data confidentiality and integrity. Future work could focus on optimizing the scaling factor and making it more efficient for real-time applications.



Responses